Viruses and worms
A "virus![]() "
"
 is a collection of computer instructions, usually small in size so that it can hide better, capable of reproducing itself, i.e.
it copies itself onto other computers on the network without the knowledge of the legitimate owner, and exploits its resources.
is a collection of computer instructions, usually small in size so that it can hide better, capable of reproducing itself, i.e.
it copies itself onto other computers on the network without the knowledge of the legitimate owner, and exploits its resources.
The virus hides by encapsulating itself in a file or in a "host" programme, but it cannot reproduce itself autonomously: in fact,
it propagates thanks to human activity, e.g. through the exchange of e-mails or infected files,
which thus provide a vehicle for spreading the virus.
In particular, the "spam" – the indiscriminate sending of a huge quantity of
"junk" mail made up of unsolicited
publicity and commercial offers – is the main way that viruses and worms are spread. The virus hides by encapsulating
itself in a file or in a "host" programme, but it cannot reproduce itself autonomously: in fact, it propagates thanks
to human activity, e.g. through the exchange of e-mails or infected files, which thus provide a vehicle for spreading the virus. In particular, the
"spam" – the indiscriminate sending of a huge quantity of "junk" mail made up of unsolicited publicity and commercial offers – is the main way that viruses and worms are spread.
In general, viruses contain various components with separate functions. For example, one part of the virus is dedicated to hiding the virus itself and avoiding means of detection (e.g. "antivirus" programmes), while another part determines the particular way in which the virus is spread. Another part, called "payload", can be of a hostile nature and includes the operations that are intended to be executed on the target. This is the part that can cause various degrees of damage to the computer in which the virus itself is inoculated. For example, it can show unwelcome messages of various kinds, it can send e-mails without the user knowing, it can delete files and prevent the computer from running correctly.
Some viruses can hide directly in the main memory (RAM![]() ) of the
calculator, or can infect particular sectors of the hard disk, activating
themselves every time the computer is switched on. In other cases the virus
itself can mutate autonomously the internal
structure in order to make it harder to detect.
) of the
calculator, or can infect particular sectors of the hard disk, activating
themselves every time the computer is switched on. In other cases the virus
itself can mutate autonomously the internal
structure in order to make it harder to detect.
If you want to avoid being "infected" it is a good idea to use special antivirus programmes which, based on the "digital fingerprint" characteristic of each virus, can almost always identify and eliminate infiltrations. It is also worth paying close attention to Internet sites visited while surfing and unexpected e-mails, which could be possible carriers.
We have talked about infection, reproduction and and propagation, terms which seem more suited to the world of biology than to the world of computers. In fact, computer viruses and biological viruses seem to have certain similarities: the former modify the code of the infected programme, which they need in order to exist, in order to reproduce. Furthermore, often the host programme can continue working undisturbed. Biological viruses too need a cell in order to survive – with a modification of its DNA, this cell is forced to reproduce the virus and continues for a certain time to maintain normal functions. Both viruses are parasites and can mutate (the software code for the computer virus and the genetic content for the biological virus) in order to make it more difficult to detect and eradicate them.
 |
"Worm![]() "
instead are
completely independent and self-sufficient programmes which, in addition to
being able to auto-reproduce, like viruses, also possess their own built-in
capacity to spread by using the network connection. They can therefore propagate
without the need for external intervention. The first worm, known as "Morris
Worm", was built and launched on Internet in 1988 and spread into thousands of
computers, creating malfunctions in communication networks even though it did
not have the specific aim of causing damage. Propagation occurred by
exploiting the weakness of some services, e.g. the electronic mail or remote
access servers (using the "rexec", "rsh" or
"finger" programmes, for example) which are normally active in a large number of
calculators. This weakness meant that the computer could be taken over
completely and subsequently the worm looked for the addresses of possible future
targets in specific system files, as
well as deciphering user passwords recorded in
the attacked computer.
"
instead are
completely independent and self-sufficient programmes which, in addition to
being able to auto-reproduce, like viruses, also possess their own built-in
capacity to spread by using the network connection. They can therefore propagate
without the need for external intervention. The first worm, known as "Morris
Worm", was built and launched on Internet in 1988 and spread into thousands of
computers, creating malfunctions in communication networks even though it did
not have the specific aim of causing damage. Propagation occurred by
exploiting the weakness of some services, e.g. the electronic mail or remote
access servers (using the "rexec", "rsh" or
"finger" programmes, for example) which are normally active in a large number of
calculators. This weakness meant that the computer could be taken over
completely and subsequently the worm looked for the addresses of possible future
targets in specific system files, as
well as deciphering user passwords recorded in
the attacked computer.
Some worms have the strange characteristic of existing and propagating only in
memory (RAM), without the need to have a file as a permanent physical support,
which makes their detection even more difficult.
Other worms are definitely nastier and contain specific functions to produce "Denials
of Service" (DoS![]() , a form of
attack that prevents the computer or one of its services from working properly
by denying access to authorised users; they can also cancel web sites. The
particularly sophisticated "MyDoom" worm
performes various functions simultaneously: it downloads and executes
arbitrary files on the compromised network node, it configures a permanent
backdoor and launches a DoS attack on a series of web sites.
, a form of
attack that prevents the computer or one of its services from working properly
by denying access to authorised users; they can also cancel web sites. The
particularly sophisticated "MyDoom" worm
performes various functions simultaneously: it downloads and executes
arbitrary files on the compromised network node, it configures a permanent
backdoor and launches a DoS attack on a series of web sites.
|
|
|
|
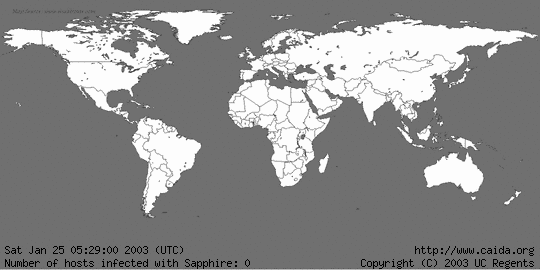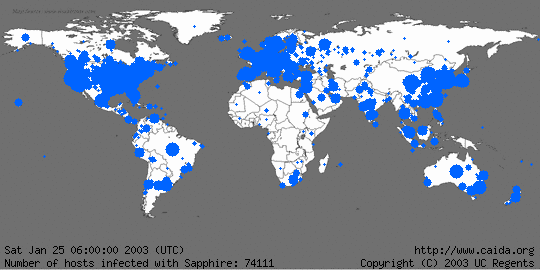
The most recent worms have reached incredible propagation speeds: the "Slammer
worm" (known also as Sapphire),
released on Saturday 25 January 2003 at 5.30 am GMT,
during its first minute of life doubled
the population of “infected” computers every 9 seconds, and after 3 minutes 55
million scan per second were executed (connection attempts aimed at compromising
other nodes). This caused immense
collateral damage in the form of a huge network overload and the consequent
clogging of communication lines. After 30 minutes the number of compromised
computers was almost 75000. It is
important to realize that if Slammer had had a more hostile
payload![]() the
consequences could have been a lot more disastrous. In the USA, Slammer even
managed to penetrate the control system of a nuclear power station (fortunately
closed for maintenance at the time) causing a delay
of about five hours in reactivating the service.
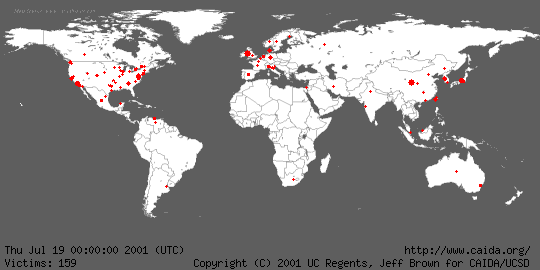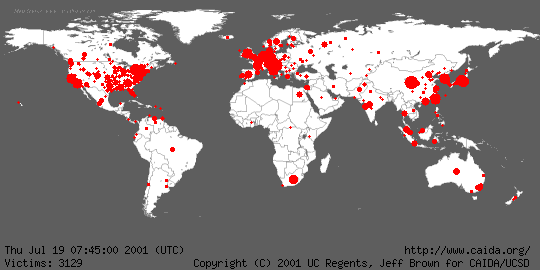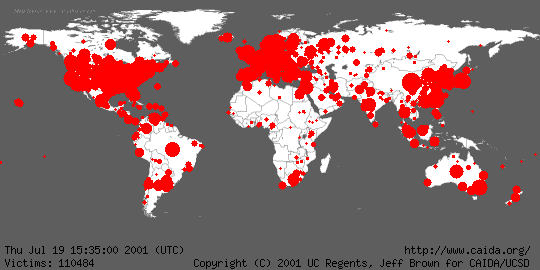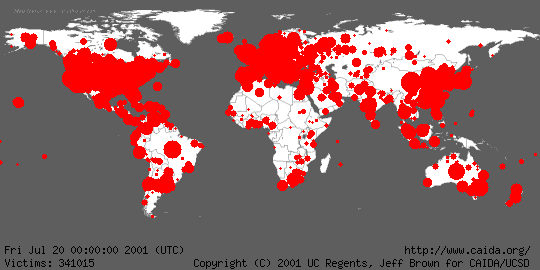
Another particularly active worm was Code Red (Fig. 2), which "infected" more
than 350,000 computers in approximately 24 hours.
the
consequences could have been a lot more disastrous. In the USA, Slammer even
managed to penetrate the control system of a nuclear power station (fortunately
closed for maintenance at the time) causing a delay
of about five hours in reactivating the service.
Another particularly active worm was Code Red (Fig. 2), which "infected" more
than 350,000 computers in approximately 24 hours.